The Ultimate Guide to Restful API (Representational State Transfer)
In today’s digital world, nothing is an island. We’re more linked up and connected than before. Even our appliances are talking amongst themselves, at this point. Linking up our devices and freeing up our data adds untold new dimensions of possibilities for every level of an organization. It also makes our workplaces and workflows infinitely more flexible… Continue reading The Ultimate Guide to Restful API (Representational State Transfer)
Read more
8 Patch Management Best Practices You Should Know About
Are you trying to learn more about effective patch management? Want to make sure that you manage patches in the best way possible? Software patching is an essential part of protecting your business and preventing cyber attacks. If your organization underestimates the importance of software patching you may be leaving your organization open to attacks… Continue reading 8 Patch Management Best Practices You Should Know About
Read more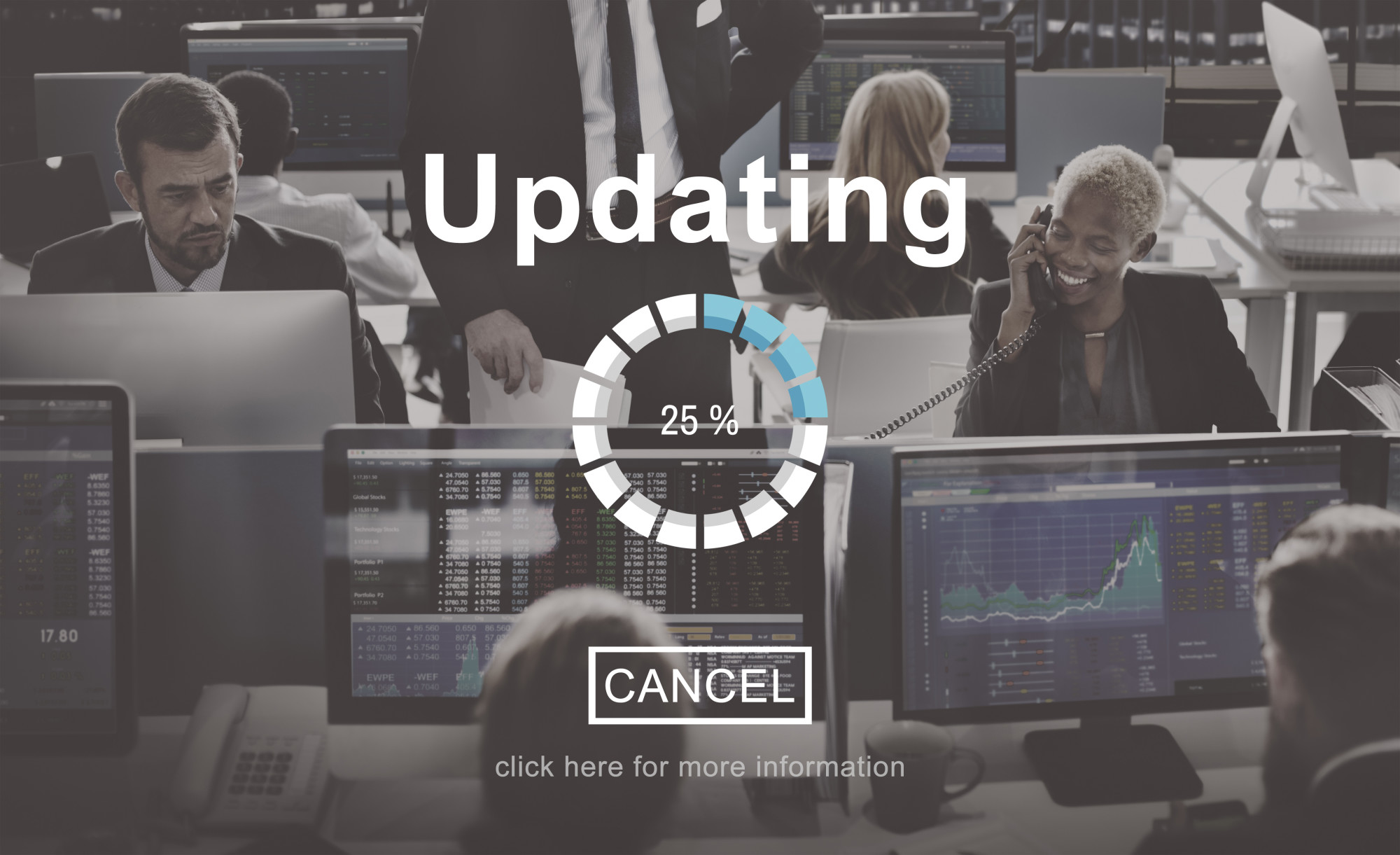
Security Operations Center Best Practices
It’s an exciting time to work in IT security. Firms face considerable challenges in defending their networks. They must also manage to protect their customer and employee data from increasingly sophisticated cyberattacks. A security operations center is also called a SOC. It’s the hub of cybersecurity for any organization. In today’s world, cyber threats such… Continue reading Security Operations Center Best Practices
Read more
How You Can Avoid Disaster With Workload Replication
If caught unprepared, natural disasters can end small businesses. Studies show that 40% of small businesses close for good after a disaster. Many natural disasters pose a threat to business operations. These include hurricanes, earthquakes, wildfires, and pandemics like COVID-19. They can destroy infrastructure and goods or impede movement. To minimize the impact of natural… Continue reading How You Can Avoid Disaster With Workload Replication
Read more
10 Benefits of IT Penetration Testing
These days, a cybercrime in some form is being committed every 32 seconds somewhere around the world. That means that chances are, you or your company may be troubled by a potential cybercrime sometime in the future. One of the best ways to prevent the impact of a potential hack lies in what’s known as… Continue reading 10 Benefits of IT Penetration Testing
Read more
What You Need to Know About Network Penetration Testing
Network penetration testing is a process that security professionals use to test security. In most cases, of an organization’s network and systems by simulating cyber-attacks. But what exactly does it entail? Well, it’s a little complicated because of the very depth of this science. However, let’s see what we can explain. The goal of this… Continue reading What You Need to Know About Network Penetration Testing
Read more
How to Help Your Company Protect Against Ransomware
Knowing how to protect against ransomware can be the difference between your company surviving or your company being destroyed. Even if you survive, an attack can leave you crippled, potentially losing you millions. It’s happened to big companies and it can happen to you. Nobody should consider themselves immune to ransomware attacks. You need to… Continue reading How to Help Your Company Protect Against Ransomware
Read more
7 Things You Should Know About Workload Replication
There are a significant number of crippling security breaches every year. These breaches result in recoveries that entail workload replication services. Hackers grow bolder and better at finding ways to break into computer systems and get data. Companies know they must have a plan of action to deal with what recovery strategies. That’s why companies try to… Continue reading 7 Things You Should Know About Workload Replication
Read more
5 Key Benefits of an Outsourced Security Operations Center
Do you want to reduce the impact of a cybersecurity attack targeted at your company? Today, 43% of cyberattacks are against small businesses, costing them an average of $200,000. If you are a small business owner, avoiding this situation is your priority. Consider outsourcing a security operations center (SOC). We’ll focus on the top five benefits… Continue reading 5 Key Benefits of an Outsourced Security Operations Center
Read more
What Is an Air-Gapped Network?
About 43% of cyber attacks target small businesses. Meanwhile, about 1 in 40 small businesses are at risk of becoming victims of cybercrimes. Unfortunately, many small businesses aren’t prepared to handle these attacks. If you’re worried about keeping your business safe this year, consider using an air-gapped network. What is an air-gapped network, exactly, and… Continue reading What Is an Air-Gapped Network?
Read more
Malware Threats: What to Watch for in 2021
About 78% of businesses lack confidence in their company’s cybersecurity posture. About 91% of businesses have increased their 2021 cybersecurity budgets as a result. Cybercrime could cost the world about $10.5 trillion every year by 2025. Is your business secure enough to withstand the latest malware threats? It helps to stay informed. Hackers are growing… Continue reading Malware Threats: What to Watch for in 2021
Read more